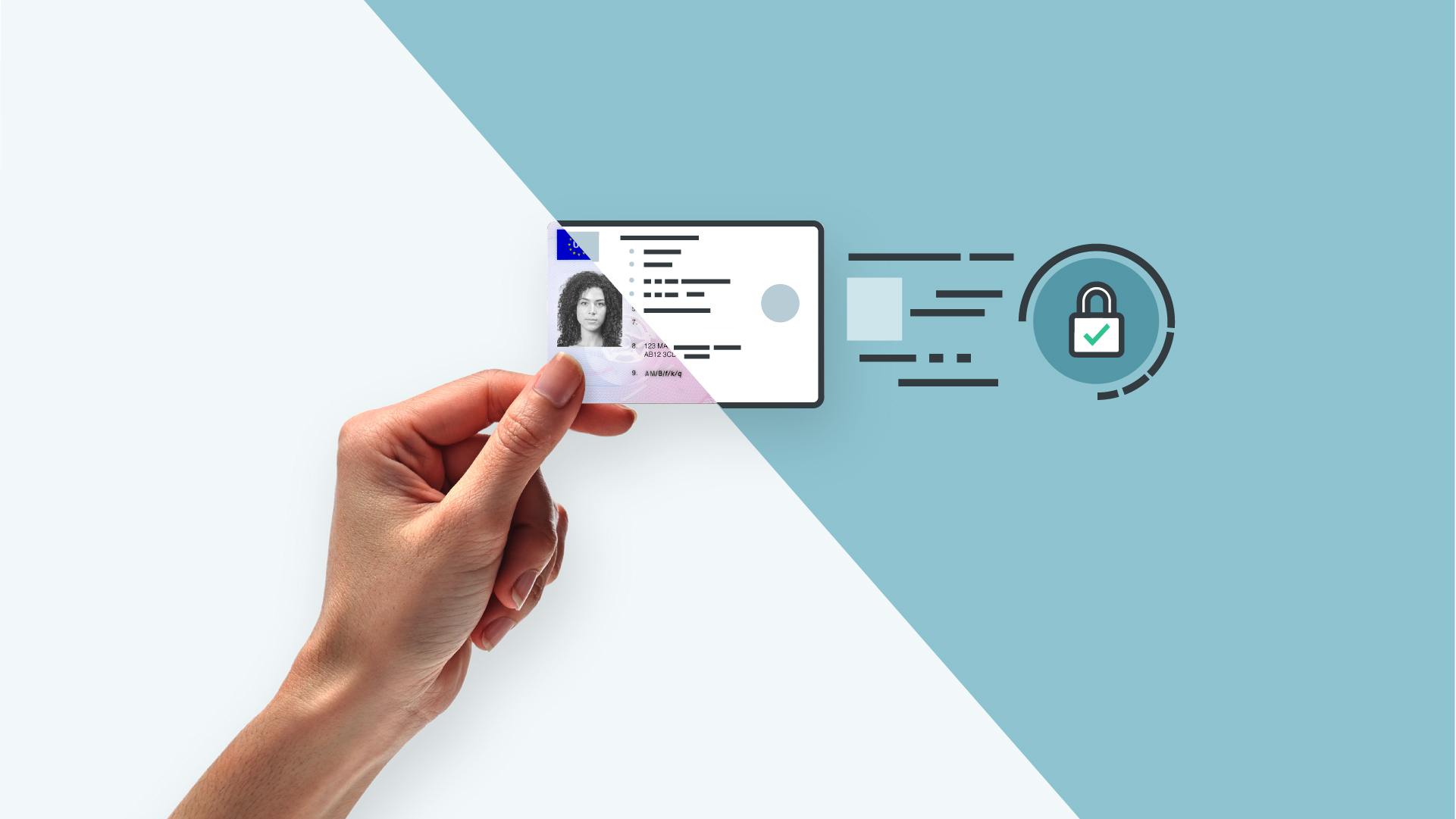
How facial biometric verification protects your customers from identity fraud
Back in the day, identity theft mostly involved fraudsters stealing personal information, such as credit card details, to commit fraud or impersonate others in person. It was a pretty straightforward game of cat and mouse between fraudsters and a business, typically carried out face-to-face. As the world has become more digitised, identity fraud has evolved to meet this digital world. One powerful solution in our arsenal against identity fraud is biometric verification. Let’s dive into what it is, how it works, and why it’s crucial for keeping your customers and online community safe. What is identity fraud? Identity
Streamline your Jersey tax returns: How to recover your Digital ID app
As the tax filing deadline approaches in Jersey, it’s time to gear up with the necessary tools for filing your returns. One such tool is the Yoti digital ID app, which offers a convenient way to verify your identity and submit your tax return online. However, many residents encounter a common hurdle: they have got a new phone or deleted the app on their current phone, only to realise they need it again to fill the latest year’s tax return. This leaves them stuck and unable to reinstall the app. But there’s a simpler solution to handle this. We’ll
Why it's time to embrace digital right to work checks
The last few years gave employers a taste of how onboarding new starters remotely can speed up their hiring. At the start of the pandemic, the Home Office amended the guidance on right to work checks, allowing them to be performed via a video call. The temporary adjustment came after employers couldn’t physically check a candidate’s ID document to prove they could work in the UK. This workaround became incredibly popular, with HR and recruitment teams noticing increased efficiency, people getting into jobs faster and reduced recruitment times. After heavy lobbying from the recruitment industry and employers, the Home Office
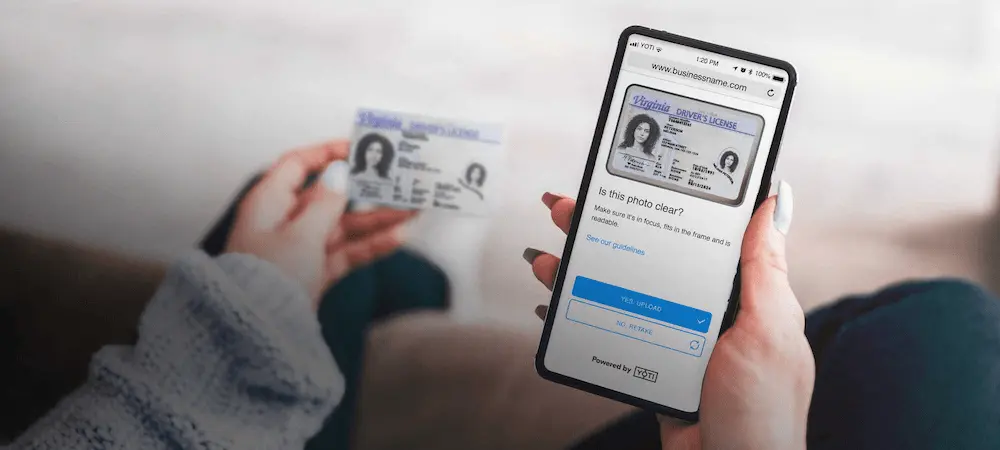
Why it’s time to automate your customer verification process
You want the digital experiences your business offers customers to be highly functional and efficient. At the same time, customers expect a seamless online experience, as well as frictionless and secure payment choices. In order to meet those needs, verifying your customer’s identity with Artificial Intelligence (AI) and machine learning should be a fundamental first step for every business to deliver better online customer onboarding processes. However, many companies are still relying on outdated processes, causing unnecessary friction for customers and exposing their businesses to errors and potential costly reputational damage. Automating certain parts of the identity verification
Explore cards - What are Yoti cards and how do we use them in the Digital ID app?
Making Yoti relevant and useful whilst preserving privacy We want to make sure that the Yoti app is useful to our whole community. We built Explore – a place where you can discover where you can use your digital ID. We also have some special offers for community members. This will look exactly the same in the Post Office EasyID app. Country-specific content In your digital ID app, you will only see content that is relevant to your country. This means that we only show you partners that you can use your digital ID with or offers
Get ahead of new age and identity verification regulations with our handy guide to know your customer (KYC) processes
It’s no longer financial institutions, real estate, art dealers, casinos, lawyers, and accountants who are the main targets for financial crimes online. Criminals are finding it harder to use them for money laundering due to rigorous regulations and effective know your customer (KYC) processes. To go undetected, they have set their sights on online multiplayer gaming, online marketplaces, FinTech, online gambling and many more small and medium businesses. Lawbreakers are attracted to these platforms because they have little to no anti-money laundering (AML) and counter-terrorist financing (CTF) regulations. For example, multiplayer online gaming platforms have experienced