Authentication
Yoti MyFace liveness white paper
Learn how Yoti’s liveness solution can help you defeat spoof attacks Liveness detection is an essential part of any verification or authentication process. It gives you reassurance that you are dealing with a real human. Read our latest white paper on liveness to learn how Yoti’s MyFace liveness solution can help defeat presentation attacks including: Paper image Mask Screen image Video imagery Deep fake video Injection attacks Bot attacks Key takeaways from the report Yoti’s MyFace solution is iBeta Level 3 approved with 100% attack detection. Why liveness is important for verification and authentication. The difference between
How we build our AI models
At Yoti, AI is not a general-purpose experiment. Instead, it is a set of purpose-built tools embedded directly into our identity, authentication and age verification products, designed to deliver secure decisions quickly while not collecting or processing unnecessary data. Rather than using large, general-purpose AI systems, we build and deploy small, specialised models that each solve a clearly defined problem. This approach gives our customers stronger security, better privacy outcomes, faster performance and greater confidence in how decisions are made. How do our AI-based checks work? At Yoti, our approach is to use multiple models to perform very
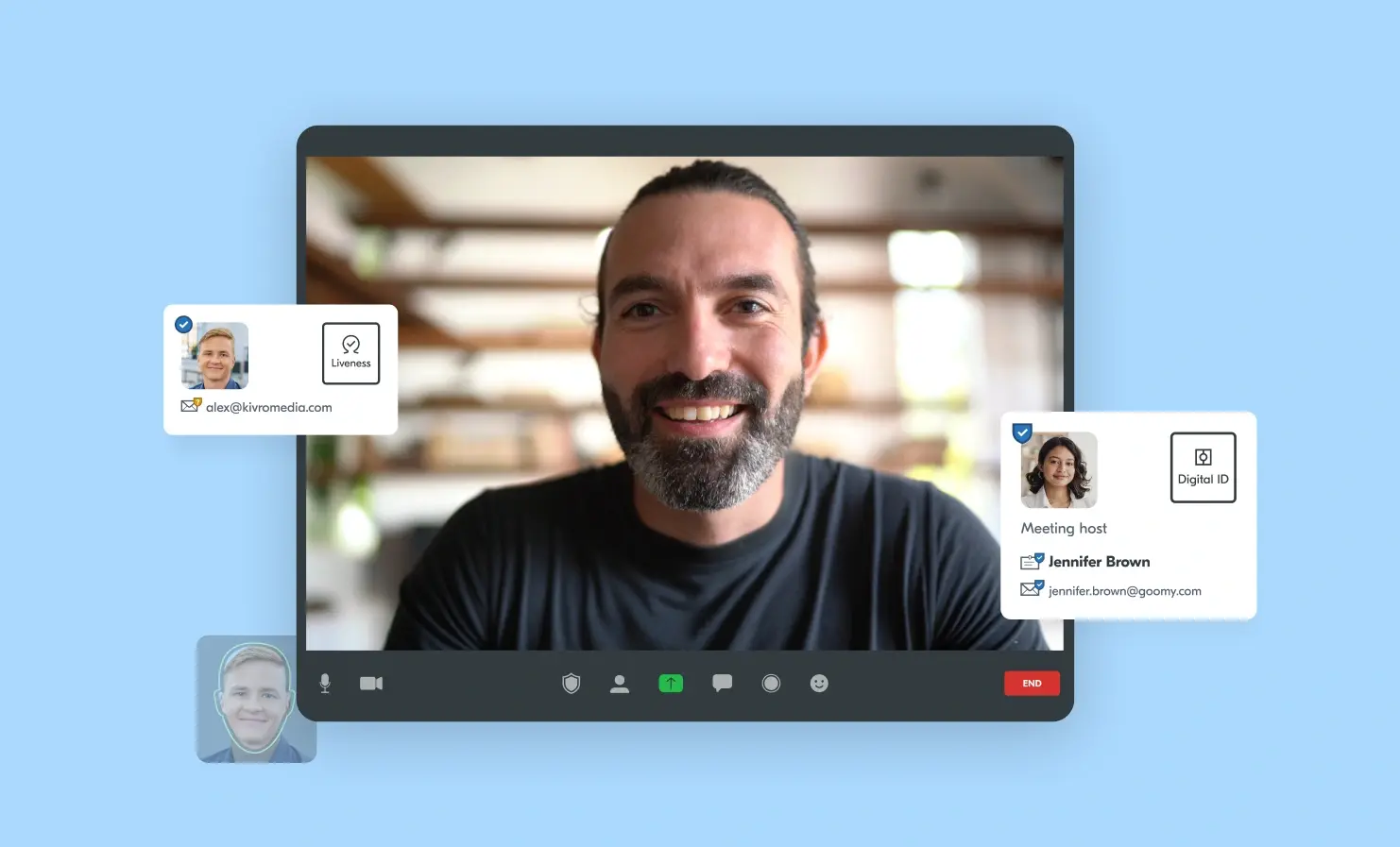
Introducing Yoti Verified Calls
Yoti Verified Calls is a new innovative service, designed to combat identity fraud and cyber attacks, while building trust during video calls. It enables businesses and individuals to verify the identity of attendees before or during video calls, reducing the risk of impersonation, deepfakes and unauthorised access. The rising threat of deepfakes Barely a week goes by without a headline about deepfakes. Whether it’s a celebrity finding fake images of them circulating online, political leaders appearing in a deepfake video, or a member of the public scammed, the technology behind deepfakes is growing more accessible, believable, sophisticated and
How strong authentication powers Zero Trust and protects against cyber threats
Until recently, organisational cybersecurity typically relied on a fortress mentality, by building a strong perimeter with firewalls and VPNs, and trusting everything inside. But in today’s digital world of cloud apps, remote work and hiring, supply chain integrations, virtual connections and sophisticated attacks, that approach is no longer enough. Once criminals breach the walls, they can often move freely and undetected. If a business can’t reliably confirm who’s accessing its systems, it leaves the door open for cyber criminals. When authentication is weak, malicious actors can: Steal employee or customer login credentials through phishing and use them to access
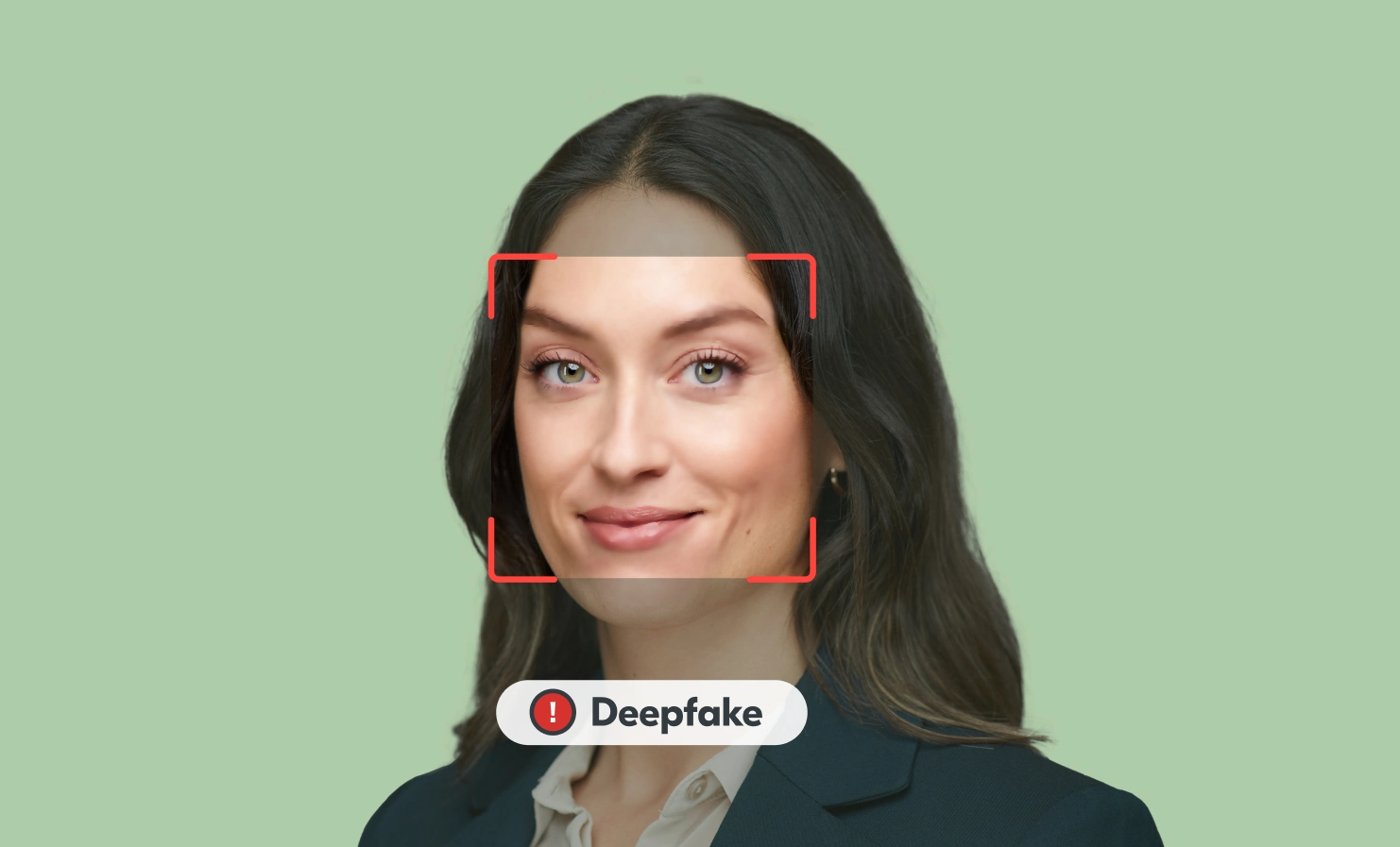
The rising challenge of detecting deepfakes
Artificial intelligence (AI) has come a long way in just a few years. What started as a tool for automating routine tasks and processing data more efficiently has now become integrated into nearly every industry. It seems as though it’s everywhere we look right now. One of the most controversial, and perhaps concerning, developments in AI is the rise of deepfakes. In simple terms, deepfakes are incredibly realistic synthetic media, such audio, video or images, generated by AI. These digital forgeries have become so convincing that telling real from fake is becoming a serious challenge. We look into how
Beyond passwords: exploring modern authentication methods for secure login
As online threats grow more sophisticated, the way we authenticate users needs to evolve. This blog explores the modern authentication methods which can support or replace passwords, such as biometrics and verified digital IDs, and how businesses can use them to protect accounts, reduce fraud and build trust with users. What is authentication? Authentication is the process of verifying that someone is who they say they are, typically before granting them access to a service or system. Traditionally, this has involved entering a username and password, something only the user should know. Are passwords enough to keep