Learn how Yoti’s liveness solution can help you defeat spoof attacks
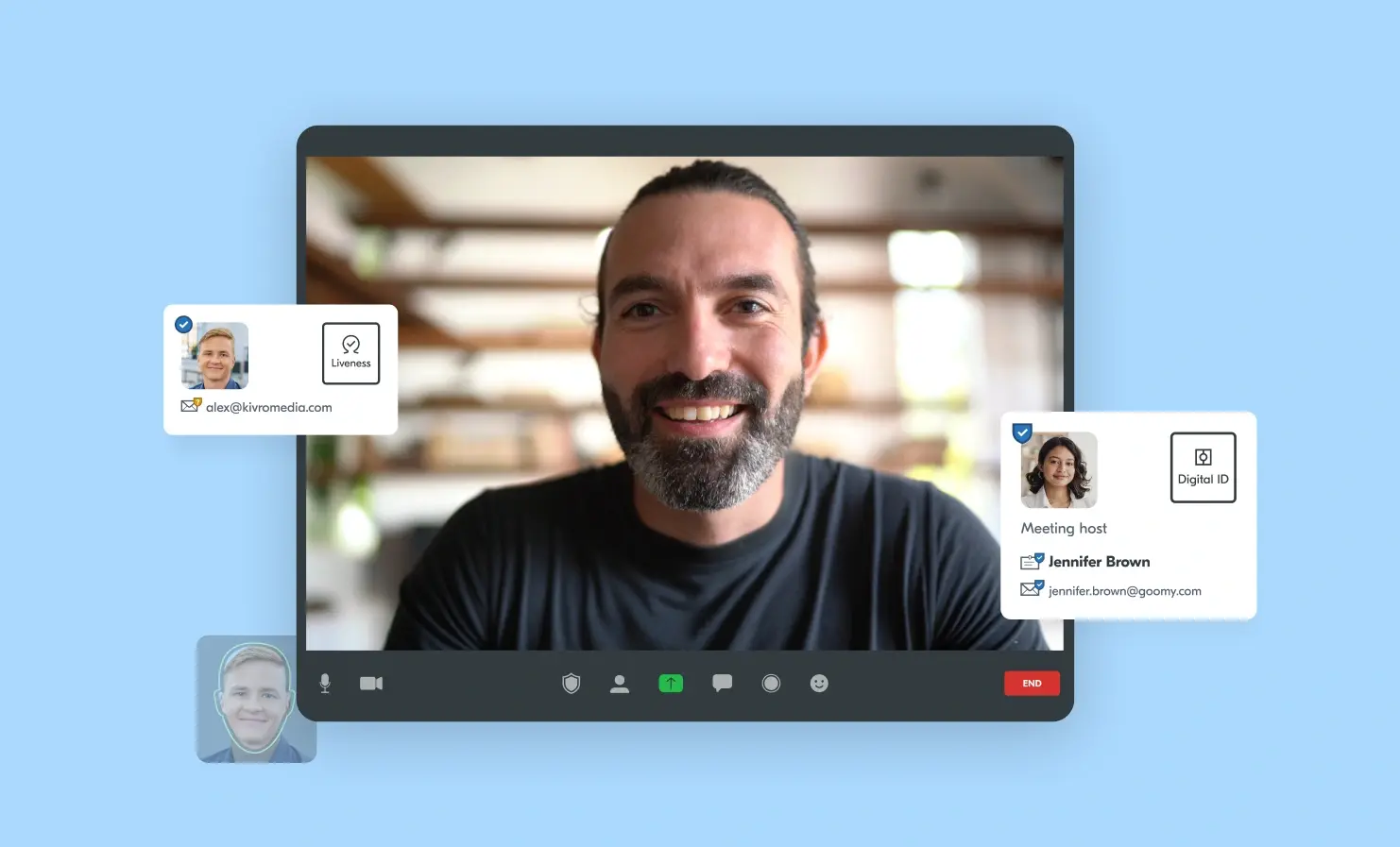
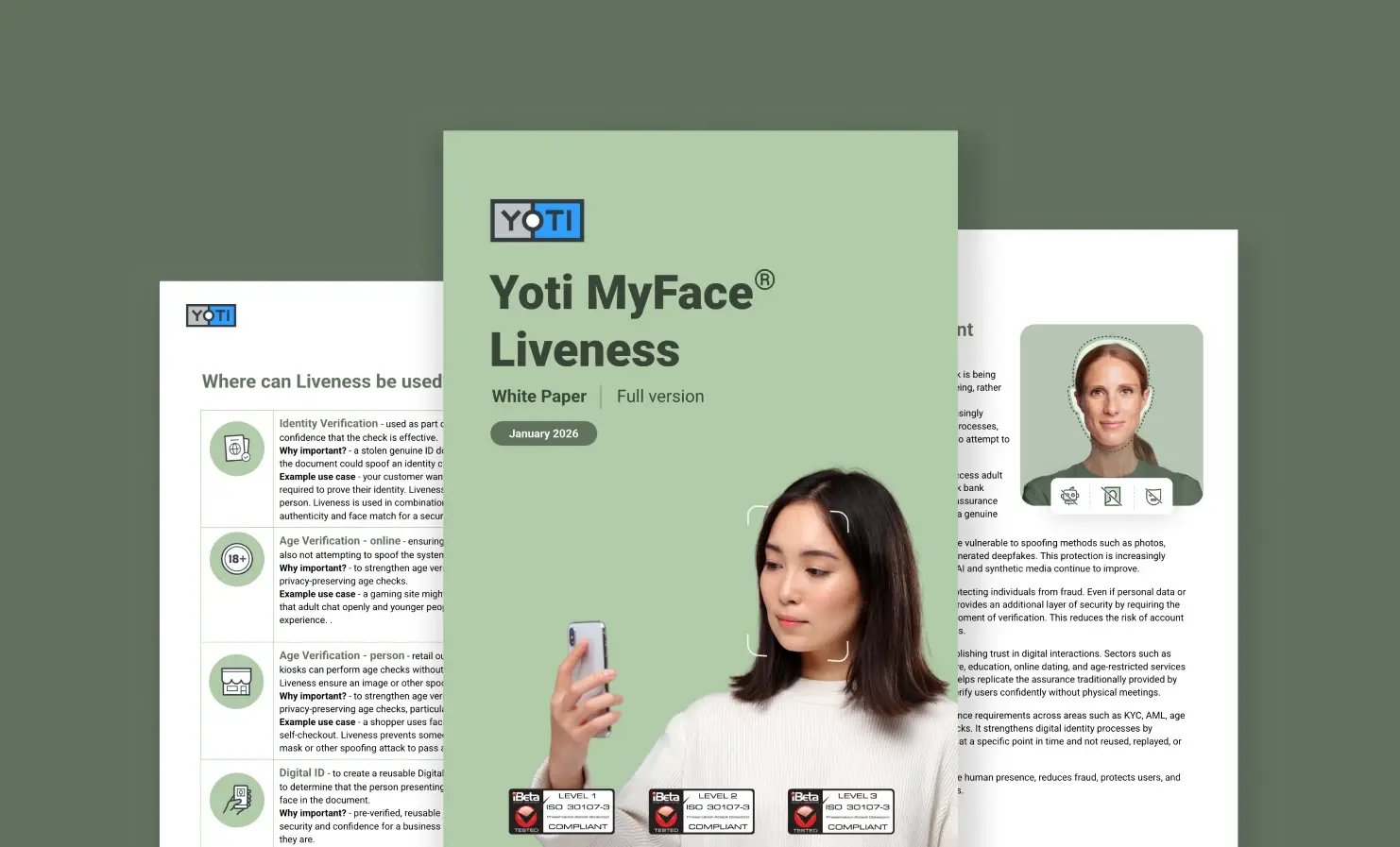
Liveness detection is an essential part of any verification or authentication process. It gives you reassurance that you are dealing with a real human. Read our latest white paper on liveness to learn how Yoti’s MyFace liveness solution can help defeat presentation attacks including:
- Paper image
- Mask
- Screen image
- Video imagery
- Deep fake video
- Injection attacks
- Bot attacks
Key takeaways from the report
- Yoti’s MyFace solution is iBeta Level 3 approved with 100% attack detection.
- Why liveness is important for verification and authentication.
- The difference between active and passive liveness.