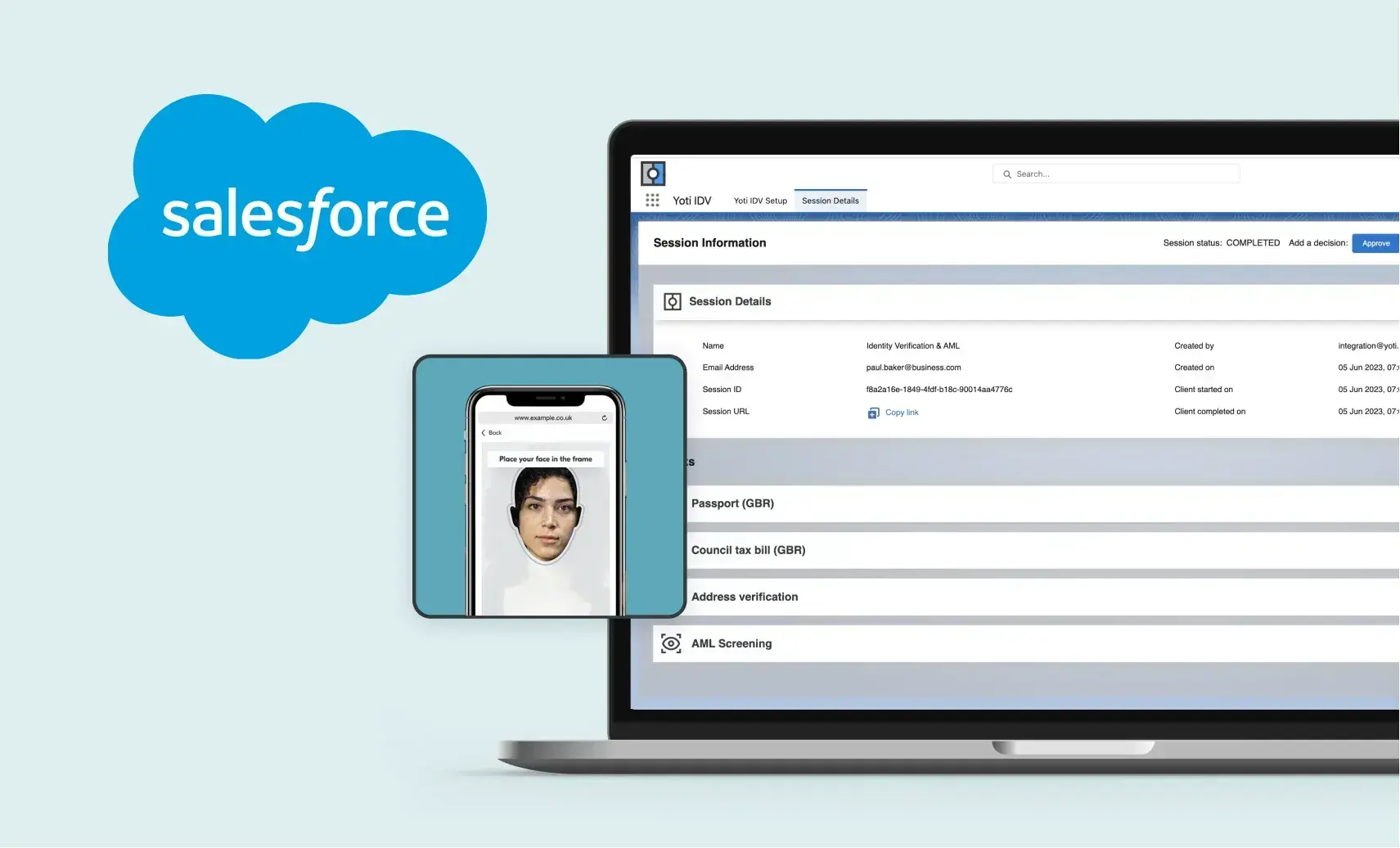
No matter your company’s size, we’re here to make verifying customers more accessible, easy and secure for you. With this in mind, we’re pleased to now offer our identity verification technology on the Salesforce AppExchange – the leading enterprise marketplace with ready-to-install apps and solutions.
It’s a ready-made solution and allows you to quickly and securely verify the identity of your customers. Armed with our ID verification, you can increase automation, fight fraud, reduce risk and stay compliant.
Start an identity check and receive the results – all in your Salesforce dashboard. This removes the need to see or store physical documents, speeds up onboarding and strengthens ID checks.
All data can be managed from your Salesforce account; improving data management and compliance policies.
This is the first step in making our solutions, including our reusable Digital ID, identity verification and eSigning, accessible globally through no-code SaaS applications.
To find out more, please get in touch.




